WiFi has become one of the most popular amenities requested by rental guests – ahead of a dishwasher or cable TV. Plain and simple: if you do not offer free WiFi, you are losing business.
Think about it...do you work when you travel? Most people reading this will answer "yes" or "I try not to, but unfortunately I do". What do you need in order to work? An Internet connection. (And a descent one at that). But it's not just for work – kids love Netflix, grandparents love to Skype, and that cat video of Fido just needs to be posted to YouTube this very second.
Did you know that rental property owners are legally responsible for everything their renters do online? If your renter engages in any illegal activities online, it is the owner who pays the price. IES has the perfect solution to your liability issue while still offering renters a seamless WiFi experience...
Our system features:
•Plug & play out of the box – 5 minute automatic activation
•Custom branded sign in page with your logo, contact information, and legal disclosure (exempting you from wrongdoing); option to add form to collect data such as email addresses, phone numbers, and birthdays for marketing purposes
•Online dashboard to get statistics such as use history, block users, generate passwords, set time limits, set speed limits, and more
•Option to charge for WiFi, or upgraded WiFi option, if desired
•Visit iesAdvisors.com/wifi for a full list of features.
Ready to learn more or make a purchase? Call 781-816-9437 or click here to email us.
Based in the historic downtown area of Plymouth, MA, IES is a web design / hosting, computer / IT support, and marketing consulting firm for small to large business, including government & nonprofits. We also sell & service POS equipment, smart systems, CCTV systems, and custom wifi service. IES operates globally via the latest technology.
Thursday, December 28, 2017
Monday, October 16, 2017
Security Notice: Key Reinstallation Attack
Background
On October 16, a WPA2 exploit was disclosed known as Key Reinstallation Attack (KRACK) that affects all WPA2 protected WiFi networks. This exploit could lead to user's WiFi traffic becoming compromised.Impact
- This exploit affects any wireless product using WPA2 encryption, which includes all IES access point products.
- Those using 802.11r or mesh repeaters are most susceptible.
- Client devices that have not received a security update specifically addressing this issue are also susceptible.
- The exploit requires physical proximity to the network.
Fix
- A new firmware version is currently under test, and we expect to qualify and publish the new version of 6.3 by end of day Tuesday, October 17. An update to 6.4 will be available at that time or shortly after.
- Once new firmware is available, all networks will begin upgrading during their scheduled maintenance window automatically
- We will also be patching older versions of our WiFi software, including 481, 590, 6.1 & 6.2, with availability end of this week.
Mitigation
- In the meantime, we have turned off 802.11r on all IES WiFi devices until they have received the firmware update
- End users should contact their WiFi client device manufacturers for security updates related to their specific client devices.
Questions / Feedback
If you have any questions or concerns about this vulnerability or the upgrade process, please reach out to IES support.
Labels:
#hack,
802.11,
802.11r,
hack,
hacking,
insecure wifi,
Key Reinstallation Attack,
KRACK,
Wi-Fi,
wifi,
wifi attack,
wifi hack,
WPA,
WPA2
Sunday, September 10, 2017
Welcome to 2017 where hacking is what seems like an everyday occurrence. Cough, cough - Equifax.
Target, CNN, HBO, Chipotle, Gamestop, Equifax - what do all these companies have in common? They have all been hacked this year.
But why, in our opinion, is the Equifax hack the worst? Well, many know Equifax as one of the top three credit reporting agencies. Ever applies for a home loan or an auto loan? Chances are the bank you are using has run your credit through Equifax. Equifax is reporting that sensitive information, such as Social Security numbers and addresses, of up to 143 million Americans has been exposed. The data breach is among the worst ever because of the amount of people affected and the sensitive type of information exposed.
Unlike other data breaches, those affected by the breach may not even know they're customers of the company, as the company gets its data from credit card companies, banks, retailers and lenders - sometimes without you knowing.
When did this happen?
Equifax said the breach happened between mid-May and July. It discovered the hack on July 29. It informed the public on September 7.
How did this happen?
Equifax said criminals "exploited a U.S. website application vulnerability to gain access to certain files."
Am I at risk, and what is Equifax doing to help?
Equifax is proposing that customers sign up for credit file monitoring and identity theft protection. It is giving free service for one year through its TrustedID Premier business, regardless of whether you've been impacted by the hack.
To enroll and / or check whether you were affected, visit www.equifaxsecurity2017.com and click on the Check Potential Impact tab. You'll need to provide your last name and the last six digits of your social security number. Once submitted, you will receive a message indicating whether you've been affected. (Giving your personal information to a company that was just hacked...ironic, we know). Then, you have the option to enroll in the program, but you can't actually sign up for the service until next week. Each customer is provided an enrollment date starting earliest on Monday.
Can I sue Equifax?
If you sign up for Equifax's offer of free identity theft protection and credit file monitoring, you may be limiting your rights to sue and be forced to take disputes to arbitration. But you can opt out of that provision if you notify the company in writing within 30 days. In addition, some attorneys argue that even if you don't opt out, the arbitration provision does not cover suits related to this breach.
It seems like companies are getting hacked a lot. Is this the biggest ever?
The Equifax breach is one of the largest breaches ever. Another high-profile examples include two breaches at Yahoo - the bigger one involved 1 billion accounts, the lesser impacted 500 million.
But why, in our opinion, is the Equifax hack the worst? Well, many know Equifax as one of the top three credit reporting agencies. Ever applies for a home loan or an auto loan? Chances are the bank you are using has run your credit through Equifax. Equifax is reporting that sensitive information, such as Social Security numbers and addresses, of up to 143 million Americans has been exposed. The data breach is among the worst ever because of the amount of people affected and the sensitive type of information exposed.
Unlike other data breaches, those affected by the breach may not even know they're customers of the company, as the company gets its data from credit card companies, banks, retailers and lenders - sometimes without you knowing.
When did this happen?
Equifax said the breach happened between mid-May and July. It discovered the hack on July 29. It informed the public on September 7.
How did this happen?
Equifax said criminals "exploited a U.S. website application vulnerability to gain access to certain files."
Am I at risk, and what is Equifax doing to help?
Equifax is proposing that customers sign up for credit file monitoring and identity theft protection. It is giving free service for one year through its TrustedID Premier business, regardless of whether you've been impacted by the hack.
To enroll and / or check whether you were affected, visit www.equifaxsecurity2017.com and click on the Check Potential Impact tab. You'll need to provide your last name and the last six digits of your social security number. Once submitted, you will receive a message indicating whether you've been affected. (Giving your personal information to a company that was just hacked...ironic, we know). Then, you have the option to enroll in the program, but you can't actually sign up for the service until next week. Each customer is provided an enrollment date starting earliest on Monday.
Can I sue Equifax?
If you sign up for Equifax's offer of free identity theft protection and credit file monitoring, you may be limiting your rights to sue and be forced to take disputes to arbitration. But you can opt out of that provision if you notify the company in writing within 30 days. In addition, some attorneys argue that even if you don't opt out, the arbitration provision does not cover suits related to this breach.
It seems like companies are getting hacked a lot. Is this the biggest ever?
The Equifax breach is one of the largest breaches ever. Another high-profile examples include two breaches at Yahoo - the bigger one involved 1 billion accounts, the lesser impacted 500 million.
Labels:
#hack,
biggest hack in history,
credit report,
credit report hack,
Equifax,
Equifax hack,
hack,
hacked,
hacker,
illegal hacking,
recent hacking,
social security,
website hack,
website hacking
Wednesday, August 2, 2017
The FBI has issued a security warning about IoT toys.
IoT toys have the potential to violate children’s privacy and safety,
given the amount of pertinent information the toys can collect and
store, the Federal Bureau of Investigation (FBI) warned this week in an advisory.
The sensors, microphones, data storage capabilities, cameras and other features of Internet of Things (IoT) toys are able to vacuum up extensive details about a child’s name, school, activities and even their physical location.
And if those toys are hacked, criminals could use the stolen information to harm a child, the FBI warned.
What Makes IoT Toys Vulnerable?
Data collected from interactions or conversations between children and toys are typically sent and stored by the manufacturer or developer via a server or a cloud service. In some cases, data are also collected by third party companies that manage the voice recognition software used in the toys.
Voice recordings, toy Web application passwords, home addresses, WiFi information, and sensitive personal data could be exposed if the security of the data is not sufficiently protected with the proper use of digital certificates and encryption when it is being transmitted or stored.
Smart toys connect to the Internet either directly, through WiFi to an Internet connected wireless access point; or indirectly, via Bluetooth to an Android or iOS device that is connected to the Internet.
Key factors affecting the user’s security include: the cyber security features, the toy’s partner applications and the WiFi network through which the toy connects.
Superior communications connections - where data is encrypted between the toy, WiFi access points, and Internet servers that store data or interact with the toy - are crucial to mitigate the risk of hackers exploiting the toy or eavesdropping on conversations or audio messages.
The FBI notes that Bluetooth connected toys that do not have authentication requirements (such as PINs or passwords) pose risks for unauthorized access, enabling criminals to communicate with children.
What You Can Do To Protect Your Child
The sensors, microphones, data storage capabilities, cameras and other features of Internet of Things (IoT) toys are able to vacuum up extensive details about a child’s name, school, activities and even their physical location.
And if those toys are hacked, criminals could use the stolen information to harm a child, the FBI warned.
What Makes IoT Toys Vulnerable?
Data collected from interactions or conversations between children and toys are typically sent and stored by the manufacturer or developer via a server or a cloud service. In some cases, data are also collected by third party companies that manage the voice recognition software used in the toys.
Voice recordings, toy Web application passwords, home addresses, WiFi information, and sensitive personal data could be exposed if the security of the data is not sufficiently protected with the proper use of digital certificates and encryption when it is being transmitted or stored.
Smart toys connect to the Internet either directly, through WiFi to an Internet connected wireless access point; or indirectly, via Bluetooth to an Android or iOS device that is connected to the Internet.
Key factors affecting the user’s security include: the cyber security features, the toy’s partner applications and the WiFi network through which the toy connects.
Superior communications connections - where data is encrypted between the toy, WiFi access points, and Internet servers that store data or interact with the toy - are crucial to mitigate the risk of hackers exploiting the toy or eavesdropping on conversations or audio messages.
The FBI notes that Bluetooth connected toys that do not have authentication requirements (such as PINs or passwords) pose risks for unauthorized access, enabling criminals to communicate with children.
What You Can Do To Protect Your Child
- Choose IoT toys very carefully by doing lots of research. Look for any known reported security issues regarding a toy.
- Find out if a toy can receive firmware or software updates and security patches - and ensure the toy is running on the latest version.
- Closely monitor your child’s activities with each toy through the toy’s parent application, if such a capability exists.
- Ensure the toy is turned off when it is not in use.
- Create a strong and unique login password when establishing a user account. For extra strong passwords, use lower and upper case letters, numbers and special characters.
- Provide only what is minimally required for creating a user account.
Labels:
#hack,
Bluetooth,
child,
child's toy,
children,
FBI,
FBI warning,
hack,
hacking,
Internet,
Internet Of Things,
IoT,
IoT toy,
toy hack,
Web,
wifi
Monday, July 24, 2017
RIP Microsoft Paint
Microsoft's graphics program Paint has been included in a list of Windows 10 features that will be either removed or no longer developed.
Paint has been part of the Windows operating system since its release in 1985 and is known for its simplicity and basic artistic results.
Paint's successor, Paint 3D, will still be available.
The list was issued as part of the Windows 10 Fall Creators Update, which rolls out in the autumn.
Microsoft says that features on the list will be either removed from Windows 10 or "not in active development and might be removed in future releases".
Other features facing the axe include the Outlook Express email client, which is replaced with the built-in Mail app, and the Reader app, which will be integrated into Microsoft Edge.
The BBC has contacted Microsoft for comment.
Welsh YouTuber Chaotic described Paint as "the greatest thing to have ever existed".
The artist known as Jim'll Paint It uses the program to create artwork on outlandish themes, commissioned by strangers. He has nearly 700,000 followers on Facebook.
"Paint hasn't been all that since they messed about with it anyway. I'm running XP on a virtual machine because it's the best one," he tweeted.
"They should just release the source and make it public domain," tweeted games developer Mike Dailly, creator of Lemmings and Grand Theft Auto.
One thing is for sure, Paint, you will be missed.
Paint has been part of the Windows operating system since its release in 1985 and is known for its simplicity and basic artistic results.
Paint's successor, Paint 3D, will still be available.
The list was issued as part of the Windows 10 Fall Creators Update, which rolls out in the autumn.
Microsoft says that features on the list will be either removed from Windows 10 or "not in active development and might be removed in future releases".
Other features facing the axe include the Outlook Express email client, which is replaced with the built-in Mail app, and the Reader app, which will be integrated into Microsoft Edge.
The BBC has contacted Microsoft for comment.
RIP Paint
People have expressed disappointment at the news on social media, with many tweeting "RIP" messages.Welsh YouTuber Chaotic described Paint as "the greatest thing to have ever existed".
The artist known as Jim'll Paint It uses the program to create artwork on outlandish themes, commissioned by strangers. He has nearly 700,000 followers on Facebook.
"Paint hasn't been all that since they messed about with it anyway. I'm running XP on a virtual machine because it's the best one," he tweeted.
"They should just release the source and make it public domain," tweeted games developer Mike Dailly, creator of Lemmings and Grand Theft Auto.
One thing is for sure, Paint, you will be missed.
Labels:
Microsoft,
Microsoft Paint,
Paint,
Paint 3D,
RIP Paint,
Windows,
Windows 10,
Windows Paint
Tuesday, June 20, 2017
Watch out Mac owners...Someone is offering Mac ransomware on the Dark Web!
In the wake of the WannaCry, a flawed piece of malware that spread virally that could've done much more damage than it did, it seems like everyone wants to jump on the ransomware bandwagon.
And if you're a malware developer, what better place to try your luck if not with Mac computers, where most user still believe they are safe by default and seem to have their guard down? That seems to be the thinking of an unknown cyber criminal who developed two new type of malicious software for Apple computers: MacSpy and MacRansom.
Despite some people's misguided beliefs (fueled in part by Apple's marketing) there's been plenty of Mac malware, even ransomware. But MacRansom and MacSpy show once again that bad guys are starting to target Macs more and more, even offering them as a service to others.
At the end of May, an unknown cyber criminal, or group of criminals, launched two sites offering MacSpy and MacRansom as services, meaning they marketed them as malware that they would sell and then offer support for.
BleepingComputer writer Catalin Cimpanu first spotted the sites. Some researchers, as well as security firms Fortinet and AlienVault have since then analyzed the samples of the ransomware and the spyware or backdoor.
While both pieces of malware aren't that sophisticated, they prove that more and more malicious hackers want to target Macs.
The bottom line: users should not assume that just because they're using a Mac they're inherently safe.
Source: BleepingComputer
And if you're a malware developer, what better place to try your luck if not with Mac computers, where most user still believe they are safe by default and seem to have their guard down? That seems to be the thinking of an unknown cyber criminal who developed two new type of malicious software for Apple computers: MacSpy and MacRansom.
Despite some people's misguided beliefs (fueled in part by Apple's marketing) there's been plenty of Mac malware, even ransomware. But MacRansom and MacSpy show once again that bad guys are starting to target Macs more and more, even offering them as a service to others.
At the end of May, an unknown cyber criminal, or group of criminals, launched two sites offering MacSpy and MacRansom as services, meaning they marketed them as malware that they would sell and then offer support for.
BleepingComputer writer Catalin Cimpanu first spotted the sites. Some researchers, as well as security firms Fortinet and AlienVault have since then analyzed the samples of the ransomware and the spyware or backdoor.
While both pieces of malware aren't that sophisticated, they prove that more and more malicious hackers want to target Macs.
The bottom line: users should not assume that just because they're using a Mac they're inherently safe.
Source: BleepingComputer
Labels:
Apple,
Apple virus,
Mac,
Mac malware,
Mac spyware,
Mac virus,
MacRansom,
MacSpy,
malware,
spyware,
WannaCry
Monday, June 12, 2017
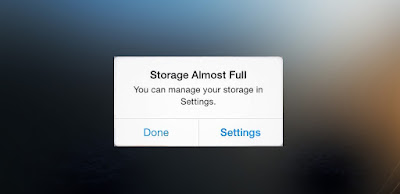
Sick of the "storage almost full" message on your iPhone? Here's how you can free up space in less than 30 seconds!
There's nothing worse than the dreaded "storage almost full"
notification and all the panic and anxiety that ensues. Trying to decide
which apps to delete can be a daunting task. So if
you're short on time, these quick cheats and easy settings adjustments
will free up space in your iPhone ASAP. That way you can get back to
watching Netflix and reacting to Facebook posts.
Set your old texts to automatically delete
There's no good reason to save that "hey what's up" message for eternity. But instead of deleting those old garbage texts one by one, simply go to Settings > Messages > Keep Messages. Decide how long you want to keep them around, and your phone deletes the oldies in one fell swoop.
Set your old texts to automatically delete
There's no good reason to save that "hey what's up" message for eternity. But instead of deleting those old garbage texts one by one, simply go to Settings > Messages > Keep Messages. Decide how long you want to keep them around, and your phone deletes the oldies in one fell swoop.
Photo Stream combines all the images you've taken on your other
devices with the photo roll on your phone, taking up precious MBs. Go to Settings > Photos & Camera, then switch off Photo Stream and revel in those sweet, sweet extra bytes.
Go to Phone > Voicemail > Edit, select old voicemails and Delete. Your phone still stores deleted voicemails for no good reason, so make sure that afterwards you scroll down to Deleted Messages > Clear All or all that hard work will have been for nothing
Delete podcasts you've already listened to
This one's going to be kind of hard to swallow, but it's time to
delete Serial off your phone. At this point, you should just assume all
parties involved are guilty. Podcasts run around 25 MBs each, so free up
some space by going to Settings > Podcasts > Delete Played Episodes.
Clear your browser cache
If you use Safari a lot, it's likely storing a ton of unnecessary web history and data to keep you browser ever-so-slightly faster. Clear that mess in Settings > Safari > Clear History and Website Data.
Purge your extraneous Instagram photos
If you use Safari a lot, it's likely storing a ton of unnecessary web history and data to keep you browser ever-so-slightly faster. Clear that mess in Settings > Safari > Clear History and Website Data.
Purge your extraneous Instagram photos
You definitely don't need a whole album full of duplicate photos that
are already readily available on Instagram. What are you going to do
with two pictures of that chicken dinner you made last night? Let it go! Go to your Photos > Edit and delete the Instagram photo album in one go.
And tell Instagram to stop saving them
This preventative measure ensures Instagram will stop saving photos in a separate album in your Photos app. Open the Instagram app > your profile > Options > unselect "Save Original Photos."
And tell Instagram to stop saving them
This preventative measure ensures Instagram will stop saving photos in a separate album in your Photos app. Open the Instagram app > your profile > Options > unselect "Save Original Photos."
Dump all that offline data
If you're a Spotify premium subscriber (or pay for similar
access to Apple Music or Slacker) you probably save certain playlists for
offline listening (so you can rock out underground during your subway
commute). But if you're in desperate need of extra space, you'll want to
scrap that luxury. There's no on-button-fix-all here; you need to
manually uncheck "Available Offline" from any playlist where you've
enabled it.

Labels:
free up space,
iPad,
iPad error,
iPad storage,
iPhone,
iPhone error,
iPhone storage,
iPhone storage almost full,
storage,
storage almost full
Tuesday, May 16, 2017
Beware: the WannaCrypt / WannaCry Ransomware
What is WannaCrypt Ransomware?
WannaCrypt Ransomware, also known by the names WannaCry, WanaCrypt0r or Wcrypt is a ransomware which targets Windows operating systems. Discovered on May 12, 2017, WannaCrypt was used in a large Cyber-attack and has since infected more than 230,000 Windows PCs in 190 countries.
How does WannaCrypt ransomware get into your computer?
As evident from its worldwide attacks, WannaCrypt first gains access to the computer system via an email attachment and thereafter can spread rapidly through your LAN network. The ransomware can encrypt your systems hard disk and attempts to exploit the SMB vulnerability to spread to random computers on the Internet via TCP port and between computers on the same network.
The best thing you can do it to avoid clicking on any attachments sent to you via email, even if they appear to be legitimate!
Although the first wave of this ransomware was stopped, we are already seeing new variations of it hitting computers around the world. Be sure your systems are consistently backing up. If you are unsure, contact your assigned IES agent.
Lastly, if you see the message below - or a similar one - it’s already too late for you. IMMEDIATELY SHUT DOWN YOUR COMPUTER and call IES at 781-816-9437.

WannaCrypt Ransomware, also known by the names WannaCry, WanaCrypt0r or Wcrypt is a ransomware which targets Windows operating systems. Discovered on May 12, 2017, WannaCrypt was used in a large Cyber-attack and has since infected more than 230,000 Windows PCs in 190 countries.
How does WannaCrypt ransomware get into your computer?
As evident from its worldwide attacks, WannaCrypt first gains access to the computer system via an email attachment and thereafter can spread rapidly through your LAN network. The ransomware can encrypt your systems hard disk and attempts to exploit the SMB vulnerability to spread to random computers on the Internet via TCP port and between computers on the same network.
The best thing you can do it to avoid clicking on any attachments sent to you via email, even if they appear to be legitimate!
Although the first wave of this ransomware was stopped, we are already seeing new variations of it hitting computers around the world. Be sure your systems are consistently backing up. If you are unsure, contact your assigned IES agent.
Lastly, if you see the message below - or a similar one - it’s already too late for you. IMMEDIATELY SHUT DOWN YOUR COMPUTER and call IES at 781-816-9437.

Labels:
cyber attack,
encryption,
encryption virus,
LAN,
network virus,
TCP,
WanaCrypt0r,
WannaCry,
WannaCrypt,
WannaCrypt Ransomware,
Wcrypt
Wednesday, April 5, 2017
IES is pleased to announce our new partnership with Heartland Payment Systems - the largest credit card processor in the United States.
Heartland Payment Systems is a Global Payments company. Global Payments Inc. (NYSE: GPN) is a leading worldwide provider of payment technology services that delivers innovative solutions driven by customer needs globally. Their technologies, partnerships and employee expertise enable them to provide a broad range of products and services that allow our customers to accept all payment types across a variety of distribution channels in many markets around the world.
Headquartered in Atlanta, Georgia with more than 8,500 employees worldwide, Global Payments is a member of the S&P 500 with merchants and partners in 29 countries throughout North America, Europe, the Asia-Pacific region and Brazil.
What Heartland Stands For
Founder of the Merchant Bill of Rights: Heartland created The Merchant Bill of Rights to promote fair credit, debit and prepaid card processing practices on behalf of owners of small- to mid-sized businesses. The aim was to create an industry standard, that calls for the clear and straightforward presentation of card processing costs. The purpose of The Merchant Bill of Rights is to enable business owners who don’t have the resources of large purchasing organizations to effectively manage their costs, determine which processor best meets their needs and realize significant savings.
Making Sure Your Money Stays in Your Hands: In 2011, legislation was passed that could mean significant savings for many businesses. The Durbin Amendment, part of the Dodd-Frank Wall Street Reform Act, placed a cap on interchange or transaction fees and was intended to provide merchants relief from card processing costs. Since the amendment was passed, Heartland has delivered every cent of savings to the rightful recipients - business owners.
“We will help businesses prosper by providing them with effective solutions in a fair, honest and transparent manner.”
– Bob Carr, Heartland’s Founder
Why IES Has Partnered With Heartland
From lodging to hospitality, restaurants, bars, clubs, convenience stores, and even the government & education sectors - Heartland processes credit cards for every industry. IES is thrilled to be able to partner with a company that holds itself to such high standards.
What This Means For IES Clients
If you are an IES client, we can help you save on your merchant processing fees. Not only do we pass along the savings to you, but if you run into trouble down the road, you know you can count on us to resolve any issues! With our partnership, we have a direct link to support personnel and a dedicated account representative to guide us through anything that is thrown our way.
The Ultimate Question
How are your credit card processing rates? Give IES a call at 781-816-9437 or email contactus@iesadvisors.com to see how we can save you on merchant fees!

Labels:
credit card processing rates,
credit card processor,
Global Payments,
GPN,
Heartland,
Heartland credit card processor,
Heartland Payment Systems,
Heartland rates,
merchant rates,
processing rates
Monday, March 20, 2017
Gigabit LTE has arrived - these are some crazy speeds!
Last week, at an event in New Orleans, Sprint, Qualcomm and Motorola
jointly announced the introduction of Gigabit LTE in the U.S. The next
frontier in cellular connectivity has been long in the making, but it’s
finally here.
At a press event, Motorola used a yet-to-be-released phone that comes fully equipped with the antenna bands and specs to support Gigabit LTE to test out the new network. This was the first device in the U.S. to test out Gigabit LTE.
The mysterious device was reaching speeds between 400 and 600Mbps. This was made all the more impressive by the location. Not only was the announcement held right before an NBA game in an arena full of people, but Sprint had ten devices running HD videos on non-stop loop, two Google Daydream stations to test out VR and the three devices running Speedtest. The network didn’t miss a beat and the devices testing out the speeds were still clocking over 500Mbps.
Gigabit LTE combines three channel carrier aggregation and 60MHz of Sprint’s 2.5 GHz spectrum with High Performance User Equipment (HPEU) and 4×4 MIMO (Multitple Input Multiple Output). What does all that mean? HPEU enhances uplink coverage for a greater range and 4×4 MIMO is the use of a new four antenna system that intelligently shifts between bands.
Representatives from Sprint stated the goal is not to reach an impressive peak speed, but sustained speeds throughout the usage of a carrier’s network. Think of it this way: It’s cool to get 50Mbps down when using a phone in an empty parking lot, but try to use a phone in a crowded place—like an arena, for instance—good luck getting anything to load. The network becomes so congested that the phone’s data connection can becomes unusable. Now imagine getting 500Mpbs down in that empty parking and in the middle of a sporting event.
When will everyone get access to Gigabit LTE? Soon, but it’ll take time. It took a tremendous amount of work by Qualcomm, Sprint and Motorola to get devices ready to test out the network yesterday, but the roll out to the masses will be much slower. We’ll need to wait for new phones that support the tech to launch, and carriers need to roll out Gigabit LTE across the nation. Qualcomm’s Snapdragon 835 chip, which supports Gigabit LTE, is expected to power the Galaxy S8, which means that phone may be the first broadly available consumer device to support next-gen networks.
At a press event, Motorola used a yet-to-be-released phone that comes fully equipped with the antenna bands and specs to support Gigabit LTE to test out the new network. This was the first device in the U.S. to test out Gigabit LTE.
The mysterious device was reaching speeds between 400 and 600Mbps. This was made all the more impressive by the location. Not only was the announcement held right before an NBA game in an arena full of people, but Sprint had ten devices running HD videos on non-stop loop, two Google Daydream stations to test out VR and the three devices running Speedtest. The network didn’t miss a beat and the devices testing out the speeds were still clocking over 500Mbps.
Gigabit LTE combines three channel carrier aggregation and 60MHz of Sprint’s 2.5 GHz spectrum with High Performance User Equipment (HPEU) and 4×4 MIMO (Multitple Input Multiple Output). What does all that mean? HPEU enhances uplink coverage for a greater range and 4×4 MIMO is the use of a new four antenna system that intelligently shifts between bands.
Representatives from Sprint stated the goal is not to reach an impressive peak speed, but sustained speeds throughout the usage of a carrier’s network. Think of it this way: It’s cool to get 50Mbps down when using a phone in an empty parking lot, but try to use a phone in a crowded place—like an arena, for instance—good luck getting anything to load. The network becomes so congested that the phone’s data connection can becomes unusable. Now imagine getting 500Mpbs down in that empty parking and in the middle of a sporting event.
When will everyone get access to Gigabit LTE? Soon, but it’ll take time. It took a tremendous amount of work by Qualcomm, Sprint and Motorola to get devices ready to test out the network yesterday, but the roll out to the masses will be much slower. We’ll need to wait for new phones that support the tech to launch, and carriers need to roll out Gigabit LTE across the nation. Qualcomm’s Snapdragon 835 chip, which supports Gigabit LTE, is expected to power the Galaxy S8, which means that phone may be the first broadly available consumer device to support next-gen networks.
Labels:
cell data,
cell phone,
cell phone data,
data,
gigabit LTE,
Internet,
Internet speed,
LTE,
LTE Plus,
Motorola,
Qualcomm,
Sprint,
Sprint gigabit data,
Sprint LTE,
Sprint LTE Plus
Friday, February 24, 2017
First there was 2G, then there was 3G, now we're on 4G. But coming soon: 5G!
Verizon announced Wednesday that it will begin testing its
fifth-generation wireless service in 11 markets across the country, from
rural areas to dense urban centers.
5G provides speeds up to 40 times faster than 4G, and it's expected to eventually impact connected everything from self-driving cars to robots.
The pilot will be available to customers in Ann Arbor, Michigan; Atlanta; Bernardsville, New Jersey; Brockton, Massachusetts; Dallas; Denver; Houston; Miami; Sacramento; Seattle; and Washington, D.C.
Verizon will begin tests during the first half of this year.
Verizon said it will select pilot customers based on their proximity to the new 5G towers and contact them about participating in the trial directly.
5G tests have been conducted for the past few years in labs and prototype environments. Now, Verizon is testing the tech that will eventually be rolled out when 5G is available everywhere, which isn't expected until 2020.
Faster broadband means you'll be able to download and consume more high-quality video. It most likely also means you'll pay more for data.

The pilot will be available to customers in Ann Arbor, Michigan; Atlanta; Bernardsville, New Jersey; Brockton, Massachusetts; Dallas; Denver; Houston; Miami; Sacramento; Seattle; and Washington, D.C.
Verizon will begin tests during the first half of this year.
Verizon said it will select pilot customers based on their proximity to the new 5G towers and contact them about participating in the trial directly.
5G tests have been conducted for the past few years in labs and prototype environments. Now, Verizon is testing the tech that will eventually be rolled out when 5G is available everywhere, which isn't expected until 2020.
Faster broadband means you'll be able to download and consume more high-quality video. It most likely also means you'll pay more for data.

Labels:
2G,
3G,
4G,
5G,
5G testing,
broadband,
cell,
cell phone,
cell phone bill,
cell phone data,
data,
data usage,
fast broadband,
Verizon
Tuesday, January 31, 2017
The “can you hear me?” phone scam is back. Here’s how to protect yourself.
Can you hear me? Don’t answer that.
The Better Business Bureau issued a press release yesterday warning the public of an an age-old scam making a comeback.
It’s been deemed the "Can You Hear Me?" scam.
In the past, this scam targeted businesses. The scammer would call - even pretend to adjust the phone or headset - and ask, "Can you hear me?"
The person on the other end would likely say, "Yes, yes, I can hear you."
With this grunt of approval, scammers could twist that around to, "Yes, the nice woman said she’d purchase this bulk of office supplies." Or, "Yes, he wants to buy an ad."
Now the phone scam is back, but it’s targeting individuals. In fact, BBB says more than half of the scams reported through its BBB Scam Tracker in the past few days have been about this one.
This is what happens: Someone calls you and you pick up. Consumers say the calls have been about anything from vacation packages to cruises to warranties.
Then the operator will ask if you can hear them, and you impulsively say "yes." But you haven’t just politely answered their questions. Rather, you’ve committed to something and didn’t even know it.
What to do if you get a "Can you hear me" call:
*Source: BBB
The Better Business Bureau issued a press release yesterday warning the public of an an age-old scam making a comeback.
It’s been deemed the "Can You Hear Me?" scam.
In the past, this scam targeted businesses. The scammer would call - even pretend to adjust the phone or headset - and ask, "Can you hear me?"
The person on the other end would likely say, "Yes, yes, I can hear you."
With this grunt of approval, scammers could twist that around to, "Yes, the nice woman said she’d purchase this bulk of office supplies." Or, "Yes, he wants to buy an ad."
Now the phone scam is back, but it’s targeting individuals. In fact, BBB says more than half of the scams reported through its BBB Scam Tracker in the past few days have been about this one.
This is what happens: Someone calls you and you pick up. Consumers say the calls have been about anything from vacation packages to cruises to warranties.
Then the operator will ask if you can hear them, and you impulsively say "yes." But you haven’t just politely answered their questions. Rather, you’ve committed to something and didn’t even know it.
What to do if you get a "Can you hear me" call:
- If someone you don't know asks "Can you hear me?" don’t say anything. Hang up.
- Stay aware of any other questions to solicit a yes. These scammers are smart; they’ll know the public has caught on and will adjust accordingly.
- Don’t answer a call from an unknown or unfamiliar number.
- Check your bank and credit card accounts on a regular basis.
*Source: BBB
Wednesday, January 25, 2017
Don't fall victim to the 'Free Wi-Fi' scam...Those wireless connections could be a trap.
The next time you're at an airport looking for a wireless hot spot, and you see one called "Free Wi-Fi" or a similar name, beware - you may end up being victimized by the latest hot-spot scam hitting airports across the country.
You could end up being the target of a "man in the middle" attack, in which a hacker is able to steal the information you send over the Internet, including usernames and passwords. And you could also have your files and identity stolen, end up with a spyware-infested PC and have your PC turned into a spam-spewing zombie. The attack could even leave your laptop open to hackers every time you turn it on, by allowing anyone to connect to it without your knowledge.
First, let's take a look at how the attack works. You go to an airport or other hot spot and fire up your PC, hoping to find a free hot spot. You see one that calls itself "Free Wi-Fi" or a similar name. You connect. That's it - you've been compromised!
The problem is that it's not really a hot spot. Instead, it's an ad hoc, peer-to-peer network, possibly set up as a trap by someone with a laptop nearby. You can use the Internet, because the attacker has set up his PC to let you browse the Internet via his connection. But because you're using his connection, all your traffic goes through his PC, so he can see everything you do online, including all the usernames and passwords you enter for financial and other Web sites.
In addition, because you've directly connected to the attack PC on a peer-to-peer basis, if you've set up your PC to allow file sharing, the attacker can have complete run of your PC, stealing files and data and planting malware on it.
You can't actually see any of this happening, so you'd be none the wiser. The hacker steals what he wants to or plants malware, then leaves, and you have no way of tracking him down.
All that is bad enough, but it might not be the end of the attack. Depending on how you've connected to that ad hoc network, the next time you turn on your PC, it may automatically broadcast the new "Free Wi-Fi" network ID to the world, and anyone nearby can connect to it in ad hoc peer-to-peer mode without your knowledge - and can do damage if you've allowed file sharing.
While some of these ad hoc networks advertising themselves as available for connection may be attributable to Windows behavior that the PC's user is unaware of, wireless ad hoc attacks may be more common that you think. Security company Authentium, Inc. has found dozens of ad hoc networks in Atlanta's airport, New York's LaGuardia, the West Palm Beach, FL, airport and Chicago's O'Hare. Internet users have reported finding them at LAX airport in Los Angeles.
Authentium did an in-depth survey of the ad hoc networks found at O'Hare, visiting on three different occasions. It found more than 20 ad hoc networks each time, with 80% of them advertising free Wi-Fi access. The company also found that many of the networks were displaying fake or misleading MAC addresses, a clear sign that they were bent on mischief.
"You connect to one of these networks at your own peril," says Corey O'Donnell, vice president of marketing at Authentium. "And you would have no way of tracking down how you were attacked, because you would have thought you were at an ordinary hot spot connection. Enterprises are also at risk, because if someone uses a corporate laptop to connect to one of these networks and gets infected, when he plugs back in to the enterprise network, the whole network is put at risk."
You could end up being the target of a "man in the middle" attack, in which a hacker is able to steal the information you send over the Internet, including usernames and passwords. And you could also have your files and identity stolen, end up with a spyware-infested PC and have your PC turned into a spam-spewing zombie. The attack could even leave your laptop open to hackers every time you turn it on, by allowing anyone to connect to it without your knowledge.
First, let's take a look at how the attack works. You go to an airport or other hot spot and fire up your PC, hoping to find a free hot spot. You see one that calls itself "Free Wi-Fi" or a similar name. You connect. That's it - you've been compromised!
The problem is that it's not really a hot spot. Instead, it's an ad hoc, peer-to-peer network, possibly set up as a trap by someone with a laptop nearby. You can use the Internet, because the attacker has set up his PC to let you browse the Internet via his connection. But because you're using his connection, all your traffic goes through his PC, so he can see everything you do online, including all the usernames and passwords you enter for financial and other Web sites.
In addition, because you've directly connected to the attack PC on a peer-to-peer basis, if you've set up your PC to allow file sharing, the attacker can have complete run of your PC, stealing files and data and planting malware on it.
You can't actually see any of this happening, so you'd be none the wiser. The hacker steals what he wants to or plants malware, then leaves, and you have no way of tracking him down.
All that is bad enough, but it might not be the end of the attack. Depending on how you've connected to that ad hoc network, the next time you turn on your PC, it may automatically broadcast the new "Free Wi-Fi" network ID to the world, and anyone nearby can connect to it in ad hoc peer-to-peer mode without your knowledge - and can do damage if you've allowed file sharing.
While some of these ad hoc networks advertising themselves as available for connection may be attributable to Windows behavior that the PC's user is unaware of, wireless ad hoc attacks may be more common that you think. Security company Authentium, Inc. has found dozens of ad hoc networks in Atlanta's airport, New York's LaGuardia, the West Palm Beach, FL, airport and Chicago's O'Hare. Internet users have reported finding them at LAX airport in Los Angeles.
Authentium did an in-depth survey of the ad hoc networks found at O'Hare, visiting on three different occasions. It found more than 20 ad hoc networks each time, with 80% of them advertising free Wi-Fi access. The company also found that many of the networks were displaying fake or misleading MAC addresses, a clear sign that they were bent on mischief.
"You connect to one of these networks at your own peril," says Corey O'Donnell, vice president of marketing at Authentium. "And you would have no way of tracking down how you were attacked, because you would have thought you were at an ordinary hot spot connection. Enterprises are also at risk, because if someone uses a corporate laptop to connect to one of these networks and gets infected, when he plugs back in to the enterprise network, the whole network is put at risk."
Labels:
ad hoc,
ad-hoc,
airport wifi,
fake wifi,
free wifi,
free wifi scam,
malware,
peer to peer,
peer to peer network,
peer-to-peer,
peer-to-peer network,
wifi,
wifi scam
Tuesday, January 17, 2017
A warning to all the selfie queens out there: you can be hacked!
Next time someone poses for a selfie with their fingers held up in a peace sign, maybe tell them to leave it at a smile.
An ordinary photo of the universal sign of goodwill might be enough for a thief to copy a fingerprint, thanks to the high quality of digital photos these days. And since Touch ID and similar technologies turn fingerprints into keys that unlock our devices and the data we keep in them, that’s cause for concern.
Just by casually making a peace sign in front of a camera, fingerprints can become widely available.
A team at the NII’s Digital Content and Media Sciences Research Division, Japan was able to reconstruct fingerprints spotted in pictures taken from up to 3 meters away.
“Fingerprint data can be re-created if fingerprints are in focus with strong lighting in a picture.” - Isao Echizen, a professor at Japan’s National Institute of Informatics
The peace sign is a common expression in social media pictures, but this technique could conceivably be applied to other common gestures like waving or giving a thumbs up. Matched with a person’s face, that makes for a significant amount of biometric data that identity thieves could do real damage with.
How Thieves Could Get Fingerprints From Selfies
The technique described by Echizen uses no special software, but does require good lighting - so for the moment you can feel free to flash whatever signs you like when the light is low. As mobile cameras become more and more powerful, though, selfies will become a bigger security liability.
The better alternative might be to make sure you aren’t relying on fingerprint security measures whenever possible. Or just avoid selfies altogether.
An ordinary photo of the universal sign of goodwill might be enough for a thief to copy a fingerprint, thanks to the high quality of digital photos these days. And since Touch ID and similar technologies turn fingerprints into keys that unlock our devices and the data we keep in them, that’s cause for concern.
Just by casually making a peace sign in front of a camera, fingerprints can become widely available.
A team at the NII’s Digital Content and Media Sciences Research Division, Japan was able to reconstruct fingerprints spotted in pictures taken from up to 3 meters away.
“Fingerprint data can be re-created if fingerprints are in focus with strong lighting in a picture.” - Isao Echizen, a professor at Japan’s National Institute of Informatics
The peace sign is a common expression in social media pictures, but this technique could conceivably be applied to other common gestures like waving or giving a thumbs up. Matched with a person’s face, that makes for a significant amount of biometric data that identity thieves could do real damage with.
How Thieves Could Get Fingerprints From Selfies
The technique described by Echizen uses no special software, but does require good lighting - so for the moment you can feel free to flash whatever signs you like when the light is low. As mobile cameras become more and more powerful, though, selfies will become a bigger security liability.
The better alternative might be to make sure you aren’t relying on fingerprint security measures whenever possible. Or just avoid selfies altogether.
Wednesday, January 11, 2017
Sure, Alec Baldwin and Missy Elliott can ask Alexa to have a dance party. But soon you may be able to tell Alexa to start your car.
By now you have seen the commercial below, which shows Amazon's Echo basic features. But did you know that more advanced features are coming soon? Ford announced Wednesday at CES 2017 that its newer vehicles will work alongside Amazon's popular Echo smart speaker and its voice assistant Alexa.
The move will allow select Ford owners to make voice requests via the Echo such as "Alexa, ask MyFord Mobile to start my car," provided they're within earshot of the smart home device.
Other capabilities include the ability to turn off the car, lock or unlock the doors and check a vehicle's battery power level. The technology could also be useful for those who want to loan a car to a friend without handing over a key. A car owner could ask its Echo to unlock and start the car, even if its miles away.
The partnership will come this month to three existing electric Fords - the Fusion Electric, Fusion Energi and C-MAX Energi - as a free upgrade to its built-in Sync 3 tech platform. Ford will roll it out the upgrade to more vehicles later in the year.
Eventually, Ford drivers will be able to make Alexa requests from directly within the car. For example, a driver could ask the technology to play an audio book or turn off their smart lights at home.
In addition to an Amazon Echo, eligible Ford owners will have to pair an Android device to Amazon's Alexa app. Meanwhile, iOS users are required to connect to the car with a physical cord. Drivers can tap the existing voice recognition button on their steering wheel to speak to Alexa.
By embracing voice commands, Ford intends to make it easier for drivers to keep their hands on the wheel and eyes on the road. The effort comes as motor vehicle fatalities spiked in 2015. Experts believe distracted driving is a key contributing factor.
Other capabilities include the ability to turn off the car, lock or unlock the doors and check a vehicle's battery power level. The technology could also be useful for those who want to loan a car to a friend without handing over a key. A car owner could ask its Echo to unlock and start the car, even if its miles away.
The partnership will come this month to three existing electric Fords - the Fusion Electric, Fusion Energi and C-MAX Energi - as a free upgrade to its built-in Sync 3 tech platform. Ford will roll it out the upgrade to more vehicles later in the year.
Eventually, Ford drivers will be able to make Alexa requests from directly within the car. For example, a driver could ask the technology to play an audio book or turn off their smart lights at home.
In addition to an Amazon Echo, eligible Ford owners will have to pair an Android device to Amazon's Alexa app. Meanwhile, iOS users are required to connect to the car with a physical cord. Drivers can tap the existing voice recognition button on their steering wheel to speak to Alexa.
By embracing voice commands, Ford intends to make it easier for drivers to keep their hands on the wheel and eyes on the road. The effort comes as motor vehicle fatalities spiked in 2015. Experts believe distracted driving is a key contributing factor.
Labels:
Alexa,
Amazon,
Amazon Echo,
app,
apps,
car,
cars,
CES,
Echo,
Ford,
Ford mobile,
MyFord,
smart home,
smart home system,
tech,
technology
Monday, January 2, 2017
Like BMW? How about transformers? If so, this is the car for you!
Antimon is a BMW 3-series car that transforms into a robot in 30
seconds. It's the work of 12 engineers and 4 technicians from Turkey,
who spent 11 months putting their creation together.
"We want to show our power all over the world. We think if we do something like this it'll get great exposure all over the world." -Turgat Alpagot, sales and marketing director for Letrons
Alpagot says he's already received bids for Antimon at this week's Big Boys Toys exhibition in the UAE capital. The highest bidder can take Antimon home at the end of the exhibition on Saturday.
The car isn't licensed for the road, and you can't drive it. But it can be moved by remote control at speeds up to 20 kilometers (12.4 miles) per hour. In its standing position, the robot can move its arms, fingers and head.
Letrons hopes Antimon will be the first in a series of 12 transformers. The rest are in the research and development stage.
Alpagot says the company has received interests from theme parks and shows looking to rent Antimon.
What's next? The creators are seeking funding from private investors to develop smaller transformers that are more affordable and can be driven on the road.

"We want to show our power all over the world. We think if we do something like this it'll get great exposure all over the world." -Turgat Alpagot, sales and marketing director for Letrons
Alpagot says he's already received bids for Antimon at this week's Big Boys Toys exhibition in the UAE capital. The highest bidder can take Antimon home at the end of the exhibition on Saturday.
The car isn't licensed for the road, and you can't drive it. But it can be moved by remote control at speeds up to 20 kilometers (12.4 miles) per hour. In its standing position, the robot can move its arms, fingers and head.
Letrons hopes Antimon will be the first in a series of 12 transformers. The rest are in the research and development stage.
Alpagot says the company has received interests from theme parks and shows looking to rent Antimon.
What's next? The creators are seeking funding from private investors to develop smaller transformers that are more affordable and can be driven on the road.

Above: Antimon - the BMW transformer made by Letrons
Labels:
Antimon,
BMW,
BMW 3,
BMW 3 series,
car,
cars,
Letrons,
remote control car,
remote transformer,
tech,
technology,
transformer
Subscribe to:
Comments (Atom)